The Mechanics of Access Control Systems
31 January 2024
The need for robust security measures has never been more critical. Access control systems play a pivotal role in safeguarding physical spaces by authorising entry and exit. This article will delve into the mechanics of access control systems, shedding light on their components, functionalities, and the role they play in enhancing overall security.
What is an Access Control System?
Access control systems are sophisticated solutions designed to manage and restrict entry to a specific room or area within a building. These systems go beyond traditional locks and keys, providing a more dynamic and adaptable approach to security. By employing various technologies, access control systems empower organisations to control who can enter, where they can go, and when.
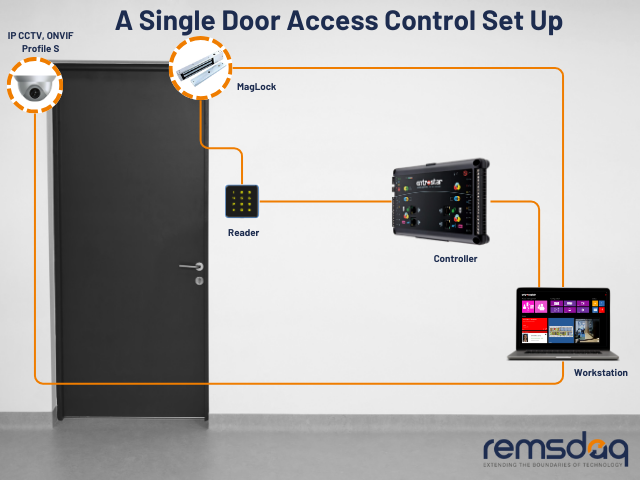
Components of Access Control Systems
Credentials
While access control systems are used to control the access of individuals to certain areas, access control credentials provide a way to authentic entry or exit. Typically, the credentials are kept on devices such as electronic access control cards, key fobs, or even mobile devices for authentication.
Access control cards contain embedded information, either in the form of a magnetic stripe, a barcode, a proximity chip, or a smart chip. This information is unique to each card and is associated with the specific permissions granted to the cardholder. When an individual presents the card to a card reader at an access point, the access control system verifies the information on the card (the credential) and determines whether the person has the right to enter the restricted area or not.
Access control key fobs can also be programmed with credential information and are both small and convenient. Access control key fobs are a core part of keyless entry systems, leveraging radio frequency identification (RFID) technology, they can be used to open and unlock doors electronically and are an alternative for some organisations to cards.
Mobile access credentials are digital credentials held within an Android or Apple iOS compatible App which turn a smartphone into a digital key. People today will almost always have a smartphone on them, making mobile access credentials (for some) a logical and convenient way of facilitating access control. Typical examples being schools, colleges and universities. The technology operates like Apple Pay or Google Pay, where a phone is held up to a digital reader and the credentials are authenticated.
Access control cards remain the primary method to carry credentials and are considered the most secure and durable. Key fobs can be more easily damaged than access control cards. Mobile credentials are not suitable for everyone, especially if an individual must use their personal mobile (rather than a company mobile).
Credential Readers
Credential verification is executed through devices called ‘readers’. These readers can be standalone devices or integrated into doors, turnstiles, or other entry points. They interpret the information on the credential carrier (card, key fob, or mobile phone) and determine whether access should be granted or not.
Biometric readers for access control are security devices that employ unique physiological characteristics, such as fingerprints, iris patterns or facial features, to verify an individual’s identity and control access to a particular area or system. During the enrolment process, the individual’s biometric data is captured and converted into a digital template, securely stored in the monitoring system.
Door Controllers
Door controllers are an integral part of an access control system. A typical door controller may be available to support 1-2 doors or modular and can be capable of expansion to control up to 8 doors. Multiple units are installed across a building over an IP network and this type of arrangement can run to several hundred doors and access points. The controllers are connected to the credential readers and request to exit buttons, as well as break glass units and can also be used to monitor third party system inputs.
Locking Mechanisms
The locking mechanism physically secures entry points. Electronic locks, magnetic locks, or even automated gates can be integrated into an access control system. These locks receive signals from the controllers, responding to access permissions accordingly.
Access Control Software
At the heart of an access control system is a software package such as EntroWatch. This stores user credential information, monitor events, generates activity reports, and controls the access system. Entrowatch maintains a comprehensive database of user information, access credentials, and permissions, facilitating real-time communication with access control controllers distributed throughout the facility. The software enforces access policies, logs events for auditing purposes, and allows for remote management, enabling administrators to update access permissions and system configurations. It can also integrate with other security systems (such as CCTV), providing a comprehensive approach to security monitoring.
How Access Control Works
Authentication
When an individual presents their credential to a reader, the authentication process begins. The reader captures the credential information, which is then sent to the controller for verification.
Verification
The controller compares the credential information with stored data kept in the monitoring system. If the information matches an authorised user’s details and meets predefined access criteria, the controller grants access.
Access Decision
Based on the verification process, the controller sends a signal to the locking mechanism. If access is approved, the locking mechanism releases, allowing entry. If denied, the door remains secure.
Assigning Roles
Role-Based Access Control (RBAC) is a widely used security case that facilitates access management by assigning roles to users based on their job responsibilities and granting permissions associated with those roles. In RBAC, access rights are defined by job functions, simplifying the administration of access control policies. Users are then assigned specific roles, and the associated permissions and restrictions are applied accordingly. This approach enhances security, scalability, and ease of administration, as changes in access levels can be managed by adjusting roles rather than individual user permissions. RBAC is especially valuable in complex systems where numerous users have varying levels of access to resources, ensuring a more streamlined and efficient access control process.
Conclusion
Access control systems are indispensable tools for organisations seeking to enhance their security posture. By leveraging advanced technologies and strategic design, these systems provide a flexible, scalable approach to regulating access and safeguarding both physical and digital assets. As the landscape of security threats evolves, access control systems continue to play a pivotal role in fortifying our environments against unauthorised access and potential breaches.
