Designing an Access Control System to Safeguard a Building
27 June 2023
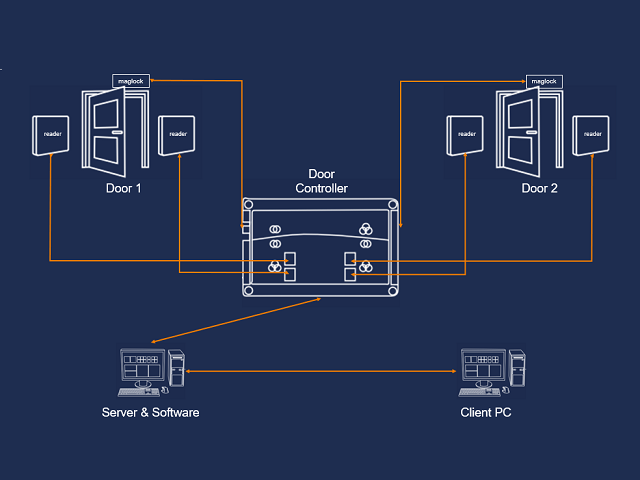
In an era where security breaches and unauthorised access pose significant threats to personal safety and valuable assets, implementing a robust access control system is vital to protect a building. An access control system controls who can enter or exit specific areas, minimising risks, ensuring only authorised personnel have access, and enhancing overall building security.
What steps do you need to consider when designing an effective access control system for a building?
Conduct a Security Assessment
Before designing an access control system, it is crucial to conduct a thorough security assessment of your building. This assessment involves identifying vulnerable areas, people, equipment, potential security risks, and understanding the specific requirements of the overall facility. Consider factors such as the building’s size, layout, number of entry points, and the sensitivity of areas that require protection. By understanding these aspects, you can tailor the access control system to meet the specific needs of the building and its users.
Define Access Control Goals and Policies
Clearly define the goals and policies of the access control system based on the security assessment. Determine who should have access to specific areas and at what times and/or days. Establish access levels and permissions based on job roles and responsibilities. Consider implementing a principle of least privilege, granting individuals only the necessary access rights to perform their duties. Create an access control policy document that outlines these guidelines and ensure all stakeholders are aware of and adhere to the policies.
Choose the Right Access Control Technologies
Selecting the appropriate access control technologies is crucial to any system’s effectiveness. Common access control technologies include:
- Card Readers and Credentials: use proximity cards, smart cards, or biometric credentials (such as fingerprints or retina scans) for identity verification.
- Door Locks and Hardware: install high-quality electronic door locks and accompanying hardware that can withstand attempts to break-in or tamper.
- Access Control Software: employ robust access control software that can manage user credentials, track access logs, and integrate with other security systems.
- Video Surveillance: integrate your access control system with video surveillance cameras to monitor and record entry points.
- Alarm Systems: link your access control system to building alarm systems to trigger alerts in case of unauthorised access attempts or security breaches.
Implement Multiple Layers of Access Control
To enhance security, consider implementing multiple layers of access control. This approach involves using different levels of security measures to restrict access. For instance, use a combination of card readers, personal identification numbers (PINs), and/or biometric authentication to verify an individual and their identity. Implementing multiple layers of access control reduces the likelihood of unauthorised entry.
Secure Critical Areas
Identify critical areas within the building that require heightened security and implement additional security measures. These areas may include R&D areas, laboratories, control rooms, finance/accounts areas with sensitive data, or storage facilities to prevent unauthorised access. Consider implementing surveillance cameras with recording capabilities, and alarm systems in these critical areas integrated into your chosen access control system,
Establish Contingency Plans
Designing an access control system should also include contingency plans for various scenarios. Create protocols for managing lost or stolen access cards, dealing with system malfunctions, and responding to security breaches. Implement backup power supplies to ensure continuous system operation during power outages. Conduct regular system tests and drills to verify the effectiveness of the contingency plans and incorporate into your business continuity plan.
Monitor and Audit
An access control system should include provisions for monitoring and auditing. Regularly review access logs to identify any suspicious activity or policy violations. Monitor system performance and ensure all components are functioning correctly. Conduct periodic audits to evaluate the effectiveness of the access control system and identify areas for improvement. The most common type of report available from an access control system is Who, Where and When. With this information you can see who is where in a building and the areas accessed regularly.
Conclusion
Designing an access control system to protect a building requires careful consideration of various factors such as the building’s layout, security risks, and access control goals. By conducting a security assessment, defining access control policies, and the selection of the most appropriate technologies. An access control system should be modular to allow for expansion using a range of door controllers (1-2 or 4-8 doors), card readers, keypads and request to exit buttons.
