How To Design An Access Control System
16 August 2018
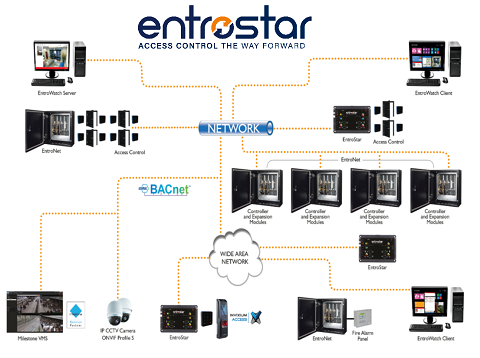
Building security, asset protection and energy management are high agenda topics for many organisations today. Companies like Remsdaq and their Access Control Systems division continue to develop their integrated security solutions to keep pace with the market innovations including biometrics, wireless locks, camera technologies and even phone-based applications and demands for greater integration into other building systems.
There are several important choices to be made when it comes to designing an access control system.
Choosing the security technologies to be installed will impact the overall operation of the system but the key to a well-managed access control system is its initial design. Access control systems provide a means to restrict and manage entry and exit to a building and rooms or spaces within it. To gain access, a person will require a credential configured for the area they want to enter. Within many companies and organisations, there are off-limits and restricted areas for employees, visitors and the public. Examples include finance departments, patient wards in hospital and medical storage facilities, accommodation blocks in universities, server rooms and data centres and hazardous manufacturing areas on industrial sites.
It is important to have an access control system that is scalable and future-proof. When one considers the number of potential visitors and users, the scale can stretch from less than 10 people to 50,000 or more. Some operators also operate access control across several sites, which adds a further level of sophistication in that they want a centralised access control management platform.
Access Control Cards
One of the first steps is a plan view of the building on which it is important to consider rooms and areas as to the level of secure access required. In conjunction the number of doors can then be calculated and assessment made of the hardware requirements in terms of credentials management and reader types.
Access control systems consist of an overall management software package, an access control panel or network of controllers installed around a building and access control proximity readers. The choice of readers will be dependent on the type of security wanted and ease of use. Access control readers fall into several categories and include card readers, biometric and mobile phone-based Apps. The classic plastic security access card remains the favoured method for many organisations as they are easy to configure and manage.
Layered Security Zones
A zoning approach is important for all building types and comes back to the point of identify which areas within a building require the most or least protection and controlled access. The installed access control system may be configured to limit access to certain times of the day either by turning access readers on or off or enabling restrictions to certain card holders based on the time of day. In a hospital or medical facility for example, a patient ward may have a different access control arrangement in the day to the ones deployed at night. Elevator controls and wireless locks can also be included within the zoned area as can biometric controls. The highest level security areas may require a combined approach of ID access card and biometrics.
A further extension of the layered zone approach is required when protecting a site with multiple building such as a university campus or multiple campus sites. Once again, a single access control database is typically used to manage credentials and authorisations but in conjunction with IP networked controllers and readers. The access management software package must be sufficiently robust to be able to manage multiple inputs without system slow down and may also have to integrate with other technologies including CCTV systems.
Cross-functional Systems Approach
The larger the facility the greater the need to take a cross-functional approach to the design and implementation of an access control system. Key functions that could play a major role include: facilities managers, building management engineers, finance, IT and HR. Within the EU, the General Data Protection Regulation (GDPR) will have to be considered with regards to the storing of personal data within the access control management software package and may also have implications if there are CCTV cameras on site.
Energy Management Systems Integration
Some access control systems like the EntroStar and EntroNet from Remsdaq use the BACnet (http://www.bacnet.org/) communications protocol and can be easily integrated into local Building Energy Management systems (BEMS). Advantages from this type if integration include greater control over energy usage (and reduced operational costs) and environmental monitoring. Access control can be used to power-up and control the ambient environment within the building depending on a person’s access control credentials. In a smart building, a swipe of card can signal to the BEMS to power-up a workstation and warm-up or cool-down a working area based on a users preferences. Office lights can also be automatically controlled in this way.
Access control systems will remain a vital security consideration for many building operators and managers in the future and greater levels of integration with other building and security systems are forecast as well as advances in reader technologies. Access control manufacturers like Remsdaq provide training for security installers, project engineering assistance and even site surveys to help ensure the right access control system is installed. For more information visit www.remsdaq.com.
